Enable App WAF
Web Application Firewall (WAF) can help fend off common attacks such as SQL injection, cross-site scripting (XSS), Web server vulnerabilities, and Trojan Horse to keep the website secure.
The following is an introduction to how to enable OpenResty-based WAF in the application of Edge Admin.
First, click to enter the Rewrite rules page:
Click the New Rule button first.
Enable the WAF module in the rules first as it is disabled by default
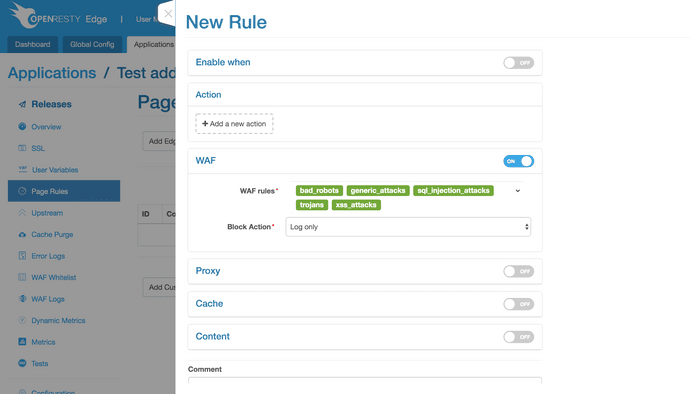
The module falls into two parts, i.e. WAF rules and triggered actions.
WAF has five built-in rule sets, namely, malicious crawlers, Trojan Horse, SQL injection, XSS attacks, and ordinary security attacks.
With WAF enabled, the five rule sets will be enabled by default. Of course, you can choose to ignore some rule sets.
You can also add your own WAF rule set or set up the WAF whitelist. Further explanation will be given later.
Below are various actions after the rule set is triggered, divided into four types:
The default setting is only recording logs without any interception or jumping;
The second type of action is jumping to the verification code page, where if the correct verification code is input, all requests of this terminal will be let through within a certain period of time.
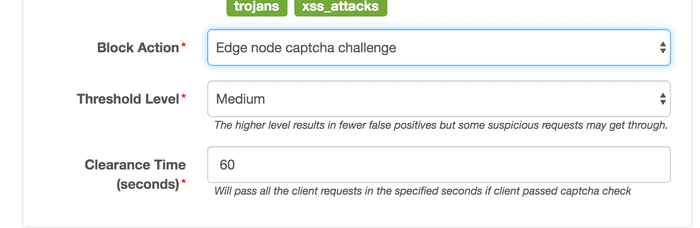
The third type of action is rejecting requests from the terminal and returning to 403.
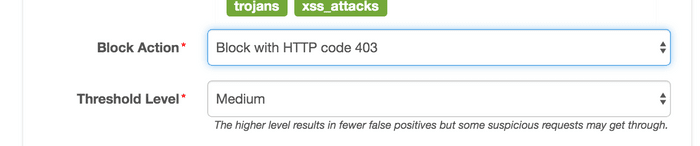
The fourth type of action is redirecting to the designated URL.
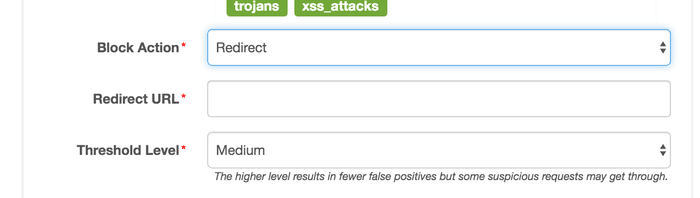
Different conditions for enabling WAF can be selected according to the request information,
For example, the following configuration can apply to enable WAF for a certain URL:
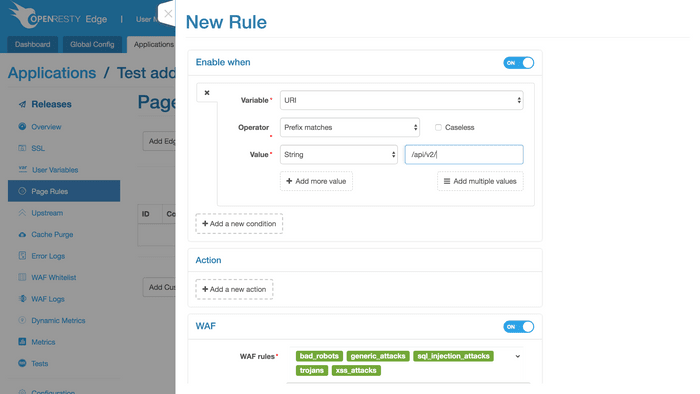
Now, a WAF rule is set successfully.
You can add multiple WAF rules, for instance, starting different WAF rule sets through different conditions and corresponding to different request prefixes.
If two WAF rules have overlapping conditions, the rule coming later (that works later) will cover the preceding one.