Cross-Site Request Forgery Protection
Introduction
Cross-site request forgery (CSRF) is a web security vulnerability that allows attackers to trick users into performing actions they do not intend to perform. OpenResty Edge provides two ways to implement CSRF protection, including setting the SameSite property of response cookies and enabling CSRF token checks.
Set response cookie SameSite
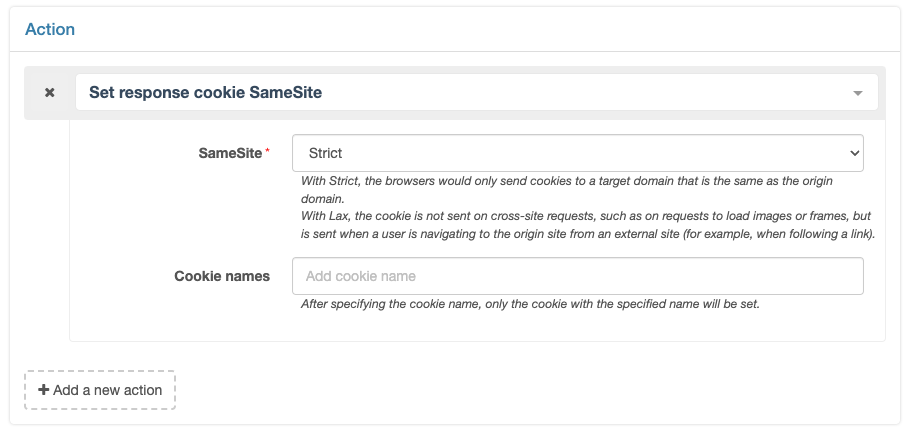
This action has the following parameters.
- SameSite: Sets the SameSite property of the cookie, either
StrictorLax.- Strict:This option indicates that cookies will only be sent by the browser on requests from the same site. If the source and destination of the request is not the same domain or protocol (even if it is a sub-domain of the same domain), the cookie will not be sent.
- Lax:This option means that cookies will be sent by the browser on requests from the same site and on secure requests (such as GET) from other sites. However, cookies will not be sent in non-secure requests (e.g. POST, PUT, DELETE, etc.) from other sites.
- Cookie names:Optional parameter to specify the cookies to be modified; if empty, all cookies will be modified by default.
Enable CSRF token
Note: This action only applies to form requests. If AJAX requests are used on your HTML pages, the CSRF token will not be successfully injected, so please turn it on as required.
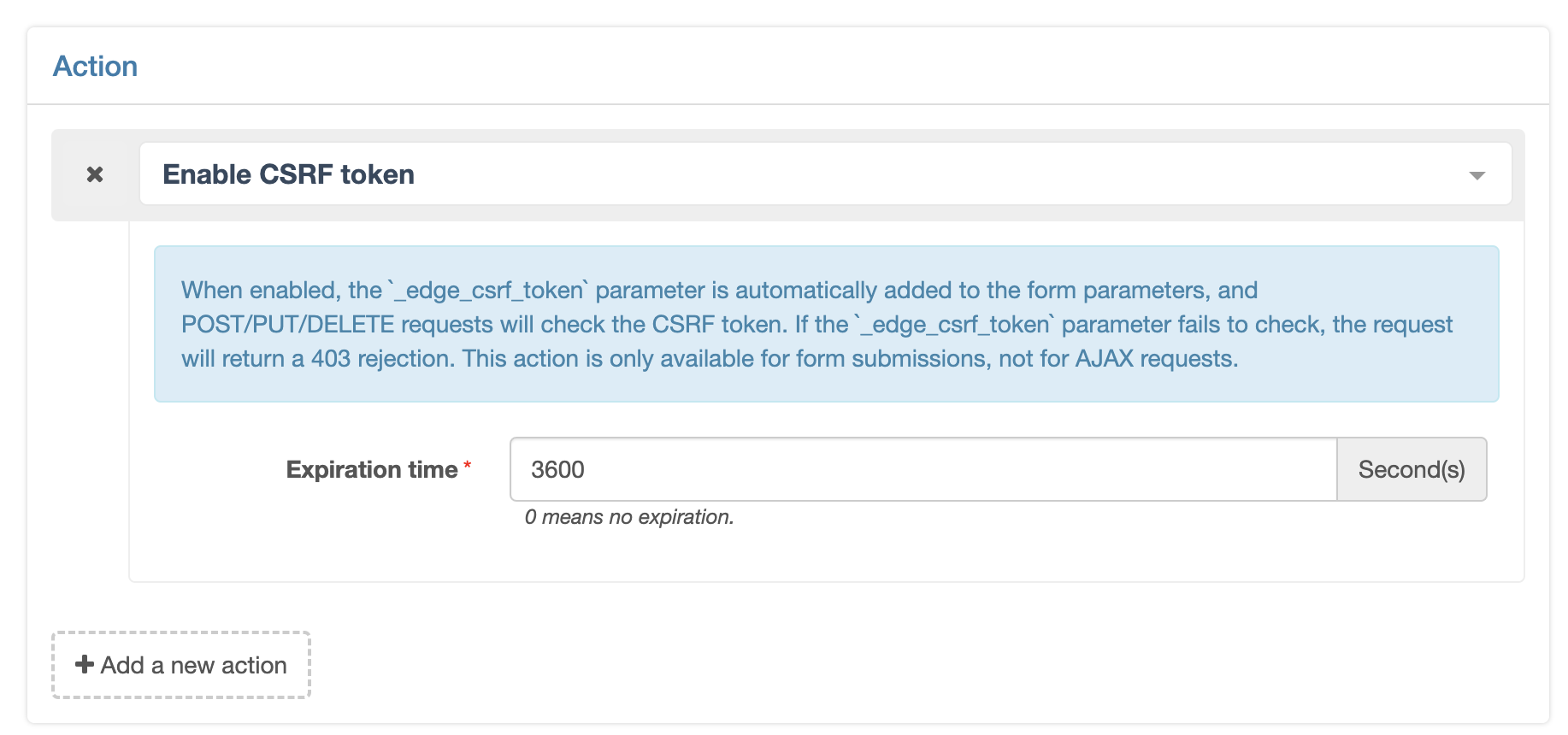
When enabled, requests with a Content-Type of text/html will have a piece of JavaScript code added to the end of the response, which will automatically inject the _edge_csrf_token parameter into the form request parameters on the page, so that it can be carried when the form request is initiated. For POST/PUT/DELETE method requests, the _edge_csrf_token in the request parameter is checked for validity and if it is invalid, a 403 rejection page is returned and the current request is recorded to the WAF log.
This action has the following parameters.
- Expiration time: it allows you to set the validity of the
_edge_csrf_tokenparameter, which defaults to 3600 seconds.