Overview
Overview
Limit Traffic and Limit Rate are common demands which could ensure the system can still provide normal services when traffic bursts or malicious attacks occur.
Below are several common scenarios for limiting traffic and rate, and all can be realized by adding rules on the Edge Admin console interface. Later we will talk about basic operations.
The fifth rule relates to responses and the other five apply to requests.
The sixth action can only take the IP address of the client side as the key word for limiting, but the other five provide more options: IP address of the client side, URI, URI parameter, and request cookie.
Please note that when these rules for traffic and rate limiting work on one application, the limiting will not spill over to other applications. This is different from what happens in NGINX.
For example, if rate limiting rules are triggered in A application for a client side, the client side can still access B application normally.
Basic Operations
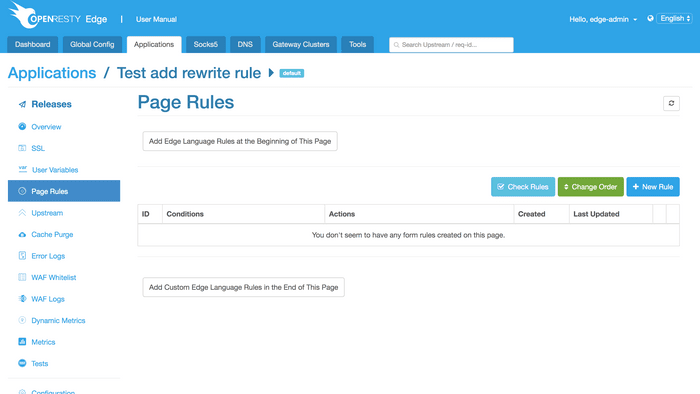
Below is the Page Rules page, offering two methods to create a rule:
Manually writing Edge language to deploy pre-configured rule set and post-configured rule set more flexibly;
Generating a rule by selecting conditions and actions on the page.
The second method is mainly used to generate rules limiting traffic and
rate. To do so, click the New Rule button.
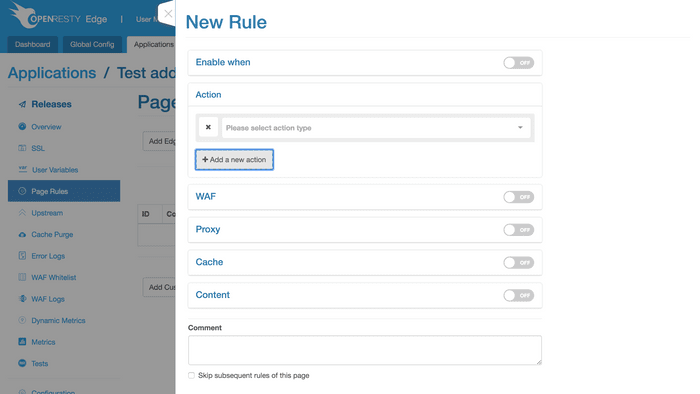
This is the New Rule page, where you can configure Action, WAF, Proxy, Cache and Content,
as well as whether to trigger the above-mentioned rules in certain conditions.
Rules for limiting traffic and rate are included in Action where you can find the first five scenarios we mentioned at the beginning.